A safety vulnerability in a stealthy Android adware operation known as Catwatchful has uncovered 1000’s of its consumers, together with its administrator.
The worm, which was once found out via safety researcher Eric Daigle, spilled the adware app’s complete database of electronic mail addresses and plaintext passwords that Catwatchful consumers use to get entry to the knowledge stolen from the telephones in their sufferers.
Catwatchful is adware masquerading as a kid tracking app that says to be “invisible and can’t be detected,” all of the whilst importing the sufferer’s telephone’s non-public contents to a dashboard viewable via the one that planted the app. The stolen information comprises the sufferers’ pictures, messages, and real-time location information. The app too can remotely faucet into the reside ambient audio from the telephone’s microphone and get entry to each entrance and rear telephone cameras.
Spy ware apps like Catwatchful are banned from the app retail outlets and depend on being downloaded and planted via somebody with bodily get entry to to an individual’s telephone. As such, those apps are regularly known as “stalkerware” (or spouseware) for his or her propensity to facilitate non-consensual surveillance of spouses and romantic companions, which is illegitimate.
Catwatchful is the most recent instance in a rising record of stalkerware operations which have been hacked, breached, or another way uncovered the knowledge they download, and is no less than the 5th adware operation this yr to have skilled an information spill. The incident presentations that consumer-grade adware continues to proliferate, regardless of being at risk of shoddy coding and safety failings that reveal each paying consumers and unsuspecting sufferers to information breaches.
Consistent with a replica of the database from early June, which TechCrunch has observed, Catwatchful had electronic mail addresses and passwords on greater than 62,000 consumers and the telephone information from 26,000 sufferers’ units.
Lots of the compromised units have been situated in Mexico, Colombia, India, Peru, Argentina, Ecuador, and Bolivia (so as of the selection of sufferers). One of the crucial information date again to 2018, the knowledge presentations.
The Catwatchful database additionally published the identification of the adware operation’s administrator, Omar Soca Charcov, a developer primarily based in Uruguay. Charcov opened our emails, however didn’t reply to our requests for remark despatched in each English and Spanish. TechCrunch requested if he was once conscious about the Catwatchful information breach, and if he plans to expose the incident to its consumers.
With none transparent indication that Charcov will expose the incident, TechCrunch equipped a replica of the Catwatchful database to information breach notification provider Have I Been Pwned.
Catwatchful website hosting adware information on Google’s servers
Daigle, a safety researcher in Canada who has prior to now investigated stalkerware abuses, detailed his findings in a weblog put up.
Consistent with Daigle, Catwatchful makes use of a personalized API, which each and every some of the planted Android apps is dependent upon to keep in touch with and ship information to Catwatchful’s servers. The adware additionally makes use of Google’s Firebase, a internet and cell building platform, to host and retailer the sufferer’s stolen telephone information, together with their pictures and ambient audio recordings.
Daigle informed TechCrunch that the API was once unauthenticated, permitting any individual on the net to have interaction with the Catwatchful consumer database while not having a login, which uncovered all the Catwatchful database of purchaser electronic mail addresses and passwords.
When contacted via TechCrunch, the internet corporate website hosting the Catwatchful API suspended the adware developer’s account, in short blockading the adware from running, however the API returned in a while HostGator. A spokesperson for HostGator, Kristen Andrews, didn’t reply to requests for remark in regards to the corporate website hosting the adware’s operations.
TechCrunch showed that Catwatchful makes use of Firebase via downloading and putting in the Catwatchful adware on a virtualized Android tool, which permits us to run the adware in an remoted sandbox with out giving it any real-world information, like our location.
We tested the community site visitors flowing out and in of the tool, which confirmed information from the telephone importing to a selected Firebase example utilized by Catwatchful to host the sufferer’s stolen information.
After TechCrunch equipped Google with copies of the Catwatchful malware, Google stated it added new protections for Google Play Offer protection to, a safety software that scans Android telephones for malicious apps, like adware. Now, Google Play Offer protection to will alert customers when it detects the Catwatchful adware or its installer on a consumer’s telephone.
TechCrunch additionally equipped Google with main points of the Firebase example desirous about storing information for the Catwatchful operation. Requested whether or not the stalkerware operation violates Firebase’s phrases of provider, Google informed TechCrunch on June 25 that it was once investigating however would now not in an instant decide to taking down the operation.
“All apps the usage of Firebase merchandise will have to abide via our phrases of provider and insurance policies. We’re investigating this actual factor, and if we discover that an app is in violation, suitable motion can be taken. Android customers that try to set up those apps are secure via Google Play Offer protection to,” stated Ed Fernandez, a spokesperson for Google.
As of newsletter, Catwatchful stays hosted on Firebase.
Opsec mistake exposes adware administrator
Like many adware operations, Catwatchful does now not publicly record its proprietor or expose who runs the operation. It’s now not unusual for stalkerware and adware operators to cover their genuine identities, given the criminal and reputational dangers related to facilitating unlawful surveillance.
However an operational safety mishap within the dataset uncovered Charcov because the operation’s administrator.
A evaluation of the Catwatchful database lists Charcov as the primary report in some of the information within the dataset. (In previous spyware-related information breaches, some operators were known via early information within the database, as oftentimes the builders are trying out the adware product on their very own units.)
The dataset integrated Charcov’s complete identify, telephone quantity, and the internet cope with of the precise Firebase example the place Catwatchful’s database is saved on Google’s servers.
Charcov’s non-public electronic mail cope with, discovered within the dataset, is identical electronic mail that he lists on his LinkedIn web page, which has since been set to non-public. Charcov additionally configured his Catwatchful administrator’s electronic mail cope with because the password restoration cope with on his non-public electronic mail account within the tournament he will get locked out, which at once hyperlinks Charcov to the Catwatchful operation.
How to take away Catwatchful adware
Whilst Catwatchful claims it “can’t be uninstalled,” there are methods to discover and take away the app from an affected tool.
Ahead of you get started, it’s vital to have a security plan in position, as disabling adware can alert the one that planted it. The Coalition Towards Stalkerware does vital paintings on this house and has assets to assist sufferers and survivors.
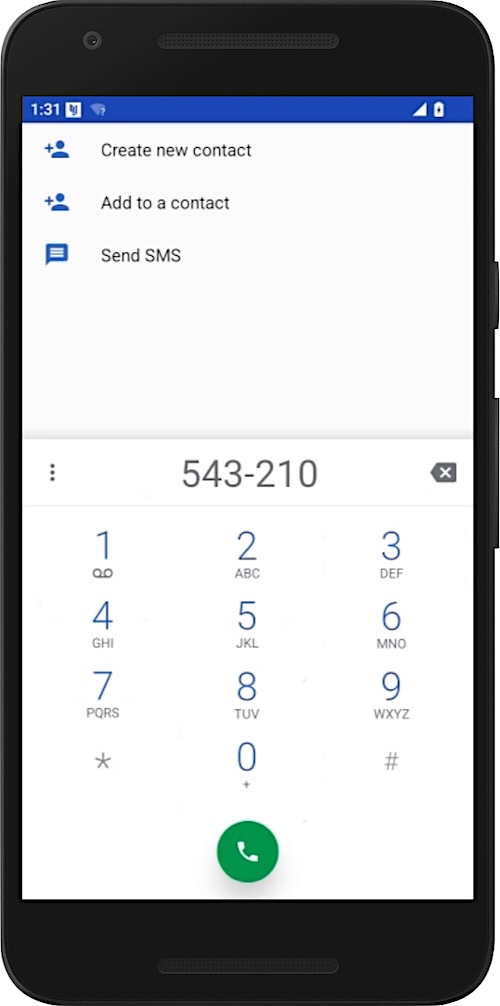
Android customers can discover Catwatchful, even supposing it’s hidden from view, via dialing 543210 into your Android telephone app’s keypad after which hitting the decision button. If Catwatchful is put in, the app must seem to your display. This code is a integrated backdoor function that permits whoever planted the app to regain get entry to to the settings as soon as the app is hidden. This code may also be utilized by any individual to look if the app is put in.


As for getting rid of the app, TechCrunch has a normal how-to information for getting rid of Android adware that let you determine and take away not unusual varieties of telephone stalkerware, after which allow the quite a lot of settings you want to protected your Android tool.
—
If you happen to or somebody you recognize wishes assist, the Nationwide Home Violence Hotline (1-800-799-7233) supplies 24/7 loose, confidential toughen to sufferers of home abuse and violence. If you’re in an emergency scenario, name 911. The Coalition Towards Stalkerware has assets in case you assume your telephone has been compromised via adware.